
In recent years and today, financial institutions have been subjected to enormous regulatory fines and ongoing on-site visits by various government regulatory agencies. Most monitoring software solutions are detecting red flags from the sender to receiver perspective and are limited to the transparency versus the new methodology of a more complex system. Through research and the development of a new methodology, we can begin to address these problems. With a new methodology we will be able to completely restrategize current trade monitoring systems from a manual and semi-automated process to an optimal one. However, before delving into how the monitoring can be improved, let us take a look at the current process and where weaknesses lie.
Description of the Letter of Credit Process
The following diagram depicts a basic flow of documents and money through a letter of credit (LC) trade process:
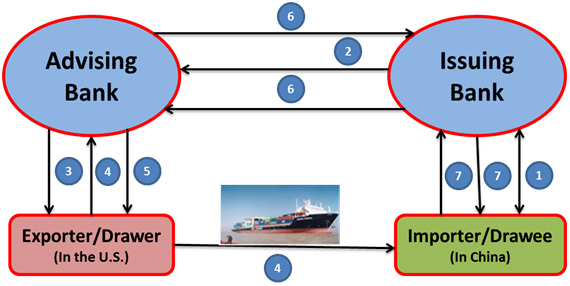
This is how the process works:
- On behalf of the importer, a LC is opened by an issuing bank.
- The issuing bank transmits the LC to the advising bank.
- Once the advising bank receives the LC, the advising bank notifies the exporter.
- Goods are delivered from the exporter to the importer, and shipping documents are provided to the advising bank.
- Upon receipt of the proper documents, the advising bank pays the exporter.
- The advising bank then sends the documents to the issuing bank, and receives reimbursement from the issuing bank.
- The issuing bank delivers the shipping documents to the importer and debits the importer’s account.
This scenario assumes that there is only an advising bank and an issuing bank, acting on behalf of both the importer and the exporter. The reality of LC processing, however, could be more complicated with additional parties involved. Those parties\entities could include: remitting bank, 1st reimbursing bank, 2nd reimbursing bank, other intermediary banks, 2nd advising bank, confirming bank, negotiating bank, shipping agent, insurance agents, pre-carriage vessels, vessels, forwarding agents, consignee, notifying parties, etc. This is where the picture becomes much more difficult. The core foundation (importer, exporter, advising bank and issuing bank) is still there, but many other elements are added. The addition of these elements, multiple financial institutions, multiple agents, multiple ways to move the goods, etc., all add a level of complexity to the notion of monitoring for money laundering.
Description of Potential Money Laundering within the LC Process
There are many ways in which money laundering could occur during the LC process. This section provides the three most common examples.
- Exclusive relationship: An exclusive relationship exists when an exporter with a history of high volume is dealing and trading with only one importer. In addition, this exporter is dealing with that singular importer by trading goods in different categories and, usually, with high dollar volumes. Under anti-money laundering (AML) guidelines, both entities are considered suspicious and should be subjects of an investigation. Enhanced due diligence (EDD), with respect to these transactions, may result in escalation and the generation of a suspicious activity report (SAR).
- Over and under invoicing: Money launderers can move money out of one country by simply using their illicit funds to purchase high-value goods. These goods are then exported to a colluding foreign partner, who then sells them in the open market at their true value. To give the transactions an air of legitimacy, the partners may use a financial institution for trade financing, which often entails LC and other documentation. For instance, when a suspect in the U.S. is in need of laundering cash received from illegal narcotic sales, he identifies a willing partner in Eastern Asia, and arranges a trade deal to legitimize his transaction through the banking system. He purchases 10 authentic Rolex watches in cash for $10,000 each, and then exports these watches to his partner with an underpriced tag of $3,000 each. The partner, in turn, sells each watch at its actual market price to legitimize these funds.
- Expected activity violation: In the case of expected activity, an exporter has a registered know your customer (KYC) profile with their commercial bank indicating trading with certain goods, and certain jurisdictions in the world are under a certain monthly dollar and quantity volume limits. Expected activity is the norm; however, when an exporter steps outside that norm, it is considered unusual and suspicious. If an exporter normally exports goods (e.g., home furniture), usually valued at about $50,000, and is consistently exporting these goods to East Asia, this is expected activity. If the same exporter suddenly begins trading in exotic cars valued at $500,000 to high-risk countries in the Middle East, this would be considered highly suspicious and an investigation would take place.
Challenges of LC AML Monitoring
Monitoring for these types of activities is extremely difficult for most financial institutions. Investigators familiar with trade-based money laundering activities are highly trained and highly skilled in identifying these activities. The primary reason this type of monitoring is so difficult is because the industry has yet to identify an “easy” way to deal with very familiar problems.
In order to identify these types of suspicious activities, financial institutions must rely on a number of different data sources. Beginning with the LC records themselves, which must be related to the bills from various sources associated with that particular LC. The information about a particular transaction then needs to take into account reference data (e.g., ISO codes, OFAC sanctioned municipalities, internal watch lists, goods codes and risk ratings, etc.). Much of this reference data is either not easily accessible and, if it is, is managed by individual investigators and analysts.
One of the biggest issues facing investigators is the generation of a ‘false positive.’ A false positive is not an accurate alert and should not be flagged for investigation. False positives result in a lower productivity for the investigator and decrease the likelihood of a ‘true positive’ being spotted. The primary reason these false positives are generated is so that the actual data being used has not been subjected to data normalization or data cleansing.
As discussed in the section on different data sources, there are a number of data sources that are input into the process of monitoring. Unfortunately, many of these data sources are historically not related to one another. For instance, there is no solution that can associate data from an LC record and its associated bill records to an individual institution’s watch list. This lack of screening leads to manual investigation and analysis and linking.
As information is updated in reference tables, there is not an easy way to make sure all of the people that need access to that updated information are notified. The inability of ‘centralizing’ reference data causes investigational delays and can result in a great deal of both work and rework.
Lastly, and perhaps the largest problem, is a question of transparency. Most investigations that occur around trade-based money laundering are so manual in nature and individual to a particular investigator, who probably follow his/her own process, that recreating an investigation is nearly impossible. Because the processes are so individualized, there is absolutely zero transparency to the financial institution.
All of these issues that financial institutions and investigators alike face result in some very adverse consequences.
Description of the Compliance Issues and Results of Non-Compliance
The evolution of monitoring financial institutions’ compliance with governmental regulations has undergone a transformation over the past several years. Prior to March 2006, a violation was a civil violation and was subject to a penalty of up to $11,000 per violation. Between March 2006 and October 2007, that civil penalty was increased to $50,000 per violation. In October 2007, as more and more violations were occurring, the civil penalty was increased to $250,000 per violation or an amount that is twice the value of the violating transaction. In addition, criminal penalties were added to the extent that an individual could be fined up to $1,000,000 and/or face imprisonment for up to 20 years.
The Financial Crimes Enforcement Network (FinCEN) and The Office of Foreign Assets Control (OFAC), a part of the U.S. Department of the Treasury, are responsible for insuring financial institutions remain in compliance with trade regulations with respect to money laundering sanctioned entities. When regulators have found that a financial institution or other institution responsible for trading with sanctioned people or countries has committed a violation, they either reach a settlement with the institution or, if a settlement cannot be reached, fine that institution. Recently, numerous domestic and foreign banks have been subject to heavy fines in the millions and billions of dollars. These are the types of penalties institutions are subjected to when they fail to properly monitor and control potentially illegal activities in their trade transactions.
Discussion of a New Methodology
As the scope of the problem financial institutions are facing begins to crystallize, what also becomes clear is that there is no technology solution on the market today that can adequately address the problem. Thus, researching and developing new methodology can begin to address the problems discussed above. It will also become apparent that the alternative to manual monitoring is to target four primary areas, discussed below.
The first area to target is the creation of an alert-based pillar that monitors for suspicious activity. The second pillar revolves around the ability to select transactions at random for investigators to audit for illicit activity. The third pillar puts a case management tool in the hands of investigators, making them more accurate. The final pillar deals with reporting and providing out-of-the-box reports that can aid investigators and institutions alike in their trade-based monitoring of both importers and exporters.
Pillars of a New Methodology
Currently, most institutions are electronically monitoring the bank-to-bank, as well as the exporter to importer, sides of trade transactions via traditional monitoring tools. These traditional monitoring tools function effectively, however, the risk of money laundering still occurs because these tools do not take into account several critical key fields involved with all parties in a trade LC transaction. The first pillar of the new methodology includes creating, and monitoring for, suspicious activity scenarios based on all the key fields involved in a trade transaction. When the methodology detects a potential red flag based on the canned scenarios, an alert is generated to enable an investigator to have immediate access to that particular transaction.
The first pillar of the methodology provides for an alert-based mechanism to give investigators a rapid view of potential suspicious activity. Another function of investigators is to examine a set of transactions selected randomly. For example, investigators may want to randomly select 1 percent of the transactions that occurred in a specified period of time, usually during a month or a quarter. The second pillar of the solution provides the ability to randomly select transactions to examine, keeping in mind that these transactions may or may not have suspicious activity tied to them.
As alerts are generated and sent to investigators, they need an easy way to manage their workflow with potential suspicious activity. The addition of the third pillar, a case management facility, is critical. This facility provides investigators with the ability to escalate, clear-and-close, or provide a basis for research into transactions with similar behavior. The case management provides a face for investigators of the underlying alerting and sampling being done.
The final pillar of the methodology includes a series of reports that are for trade AML compliance executives that allow them to gain a perspective on their current business, help identify potential areas of risk and exposure, and to see possible trends in their trade business. Reporting will be layered into the overall solution and investigators will have the ability to easily display a number of reports to aid in their research and investigation, minimizing the more traditional manual and paper-based processes currently in place. A sample inventory of some of the reports follows:
- high dollar value by goods and country (imports and exports)
- one-off transactions (imports and exports)
- amended transactions by country and goods (imports and exports)
- missing customer information (imports and exports)
- potential structured transactions (imports and exports)
- exclusive relationship (imports and exports)
Additional reports can be developed as part of the overall solution. The new methodology is comprehensive in nature and is designed to be easily deployed and configured within any financial institution.
Conclusion
Currently, the majority of monitoring surveillance systems available at most large commercial banks is the traditional wire transfer monitoring software systems. As far as we know, they do not incorporate all the fields involved in a solid trade-based monitoring system. The new mentioned methodology will gather and tie-in all of the necessary key fields in trade. So, by demand, and in a short time you can detect a trade-based AML red flag and ultimately avoid the need to retrieve the paper documents. This new methodology provides a glimpse into the business and would help identify risks and trends to improve revenue and trade products. The main challenge would be dealing with ‘dirty’ data and multiple tables that advanced sophisticated software application can succeed executing this optimum all-in-one AML trade-based monitoring and reporting methodology.










