As anti-money laundering (AML) and financial crimes compliance professionals, we are focused on preventing money laundering, terrorism financing, fraud, waste and abuse. While conducting our work, we have to recognize the vulnerabilities in our current thinking about identity verification and authentication across the entire financial institution enterprise.
The problem we have is that:
- We begin enrollment, onboarding and other Customer Identification Program/ Know Your Customer (CIP/KYC) processes with different Personal Identity Information (PII) documents that are created for different purposes and have varying reliability (e.g., driving, taxes, employment, citizenship, education, military, etc.). These documents possess different PII elements, employ different formats and levels of security, vary in period of validity, retention and sharing policies.
- Once enrollment and verification are completed, we assume in our authentication processes that the validity of the identity and the associated risks remain static. We rarely relate the identity risk to identity use and the transactions that depend upon it.
- There is rarely, if ever, a feedback loop that revalidates and adjusts identity risk based upon identity use and transactional behavior.
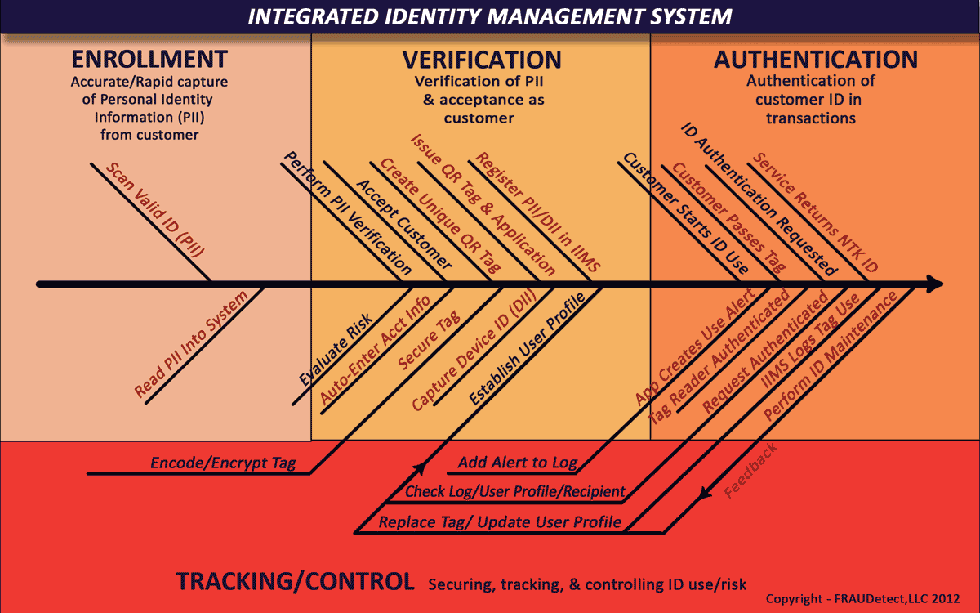
Consideration should be given to implementing an Integrated Identity Management (IIM) process that incorporates the principles of a complete system in which: input and output are measured; security is layered and diversified throughout; the most modern combinations of technology are blended; identity use and related transactions are monitored, tracked and evaluated; and a solid feedback method detects and warns of behavioral changes and risks. Such a process must incorporate cost efficiency as a principle goal and use reliable methods to reduce labor and increase both accuracy and reliability.
A new paradigm is possible that can:
- Scan PII data directly from a valid 2D bar code or identification card with a magnetic strip into a verification process. (Eliminating keystroke errors)
- Evaluate verification results and automatically enter approved PII into bank account opening forms. (Eliminating keystroke errors, duplicate entry and reducing labor
- Capture device identity information (DII) from mobile phones and marry this with PII. (Creating a new dimension of identification and tracking)
- Issue a highly secure encoded/encrypted unique quick response (QR) tag to the individual for controlled identification. (Maintaining true, verifiable identity on each transaction)
- Track transfer of identity information, monitor transactions for risk and update identification profiles. (Monitoring and adjusting for risk in identity profile and use)
The approach uses scanning and auto entry systems to capture data from a valid identity card. While using conventional PII verification methods, the IIM expands from traditional methods by adding in DII as a component of the individual's dynamic identity. The DII provides not only the specific static information for the customer's wireless device, but it also is employed later in the authentication and transaction analysis processes to provide location and other dynamic information. A unique QR Code (ID Tag) carries encoded and encrypted information about the individual's identity and is maintained on the wireless device by a high security application, or the tag can be printed on a card or used on a PC. The tag can be transmitted visually, by SMS, email or through the Internet. Since the actual identity information resides on a remote server, a series of logging, risk assessment, authentication and monitoring steps are included to ensure that risk for each transaction is assessed and feedback is provided for changes to the individual's profile.
The above fishbone chart depicts some of the functions of an IIM that will enhance AML customer risk controls and also protect against identity theft and fraud. New/added functions are in red.
As anti-money laundering and counterterrorism financing remain key government objectives for the financial industry, the complexity of both criminal methods and regulatory compliance continues to increase. Laundering and other suspicious activities, like those associated with Summer Work Program/J1 visa risks, continue to provide serious challenges for customer identification and enhanced due diligence programs.
Consider the advantages of an Integrated Identity Management System for tracking potentially high risk customers for AML compliance. The system can be implemented for all or only certain groups of customers. For example, suppose we wanted to track customers with ITINs and J1 visas. These individuals could be issued a unique tag that could reside on a cell phone, a bank identification or debit card. A printed label with the tag could be fixed to other identity documents required for use in bank transactions. By reading the tag at each transaction with the bank, the members of the group could be tracked by frequency of use, location of use (GPS), risk profile, profile (i.e., behavior) changes and transaction type.
The mobile payments industry is a driving force for the expanded use of wireless communications. At the beginning of 2012 there were 100 million smartphones in service in the U.S. and growth in this technology is expected to remain at 15 percent per year for the next five years. Within that time, the computational power in a handheld device will be equal to today's personal computer and the devices will have communication features and speeds that will further drive growth in the mobile space. One of the important features of the smartphone is its ability to display high resolution images. This is not only a value for accurately reading QR codes, but it also permits display of individual identity photos in high quality. Combining accurate, high quality facial images with a series of knowledge-based questions, obtained from a highly secure process, can produce significant improvement in assuring true identity transactions.
Customer identification can no longer be treated as an independent event at the beginning of a continuing business relationship; and then assumed to remain valid indefinitely in today's dynamic world. In addition, identity verification and authentication of customers must be holistic. Systems must address enterprise-wide needs, including diverse business and services verticals across the financial institution.
The knowledge of PII must be maintained as it evolves; it must be protected with more than simple passwords and user authentication, and must be adaptable to the rapidly evolving needs of mobile commerce. The Integrated Identity Management System described herein is a paradigm shift from the past and into the future. It recognizes the vulnerabilities of today and the needs of tomorrow by employing the latest highly mobile and responsive technology embodied in smartphones, QR codes, advanced encoding and encryption, profile and behavior analysis, and other security measures. The benefits of the approach focus on both the institution and the individual. Finally, the methods described produce a true prevention process that can eliminate the threats of identity theft and fraud and their impacts on the banking industry.