Since Bitcoin’s launch in 2009, cryptocurrency has driven new markets, spurred advancements in financial infrastructure and driven innovative thinking in how to meet the world’s economic needs. However, many stakeholders, including regulators, compliance professionals and law enforcement, still do not understand cryptocurrency or its anti-money laundering (AML) impact.
That needs to change as cryptocurrency adoption continues to grow. While research indicates that the vast majority1 of cryptocurrency transactions are for legitimate purposes, cryptocurrency’s place outside the traditional financial system gives it a special appeal to cybercriminals and other bad actors. As such, it is essential for those in the AML world to understand this emerging asset class, the risks it introduces and how to mitigate those risks.
But First, What Is Cryptocurrency?
Cryptocurrencies are digital assets commonly used as mediums of exchange or stores of value. Each cryptocurrency’s transaction history and record of user balances is recorded on a blockchain, which acts as a permanent, decentralized ledger stored across many users’ computers, ensuring the database remains intact and unchanged.
Cryptocurrency users store funds and carry out transactions using cryptocurrency wallets, which can come in both software and hardware form. Wallets contain two types of cryptographic keys, which are long, unique combinations of letters and numbers necessary to initiate transactions, similar to a password. Public keys, also known as cryptocurrency addresses, are digital, public facing “signatures” that represent a user’s intention to send or receive cryptocurrency on the blockchain. Any user can send cryptocurrency to another if they know the recipient’s public key. On the other hand, the private key is a second signature necessary to initiate a transaction from one’s own wallet; therefore, it should be known only to the wallet’s owner. Wallets typically contain many pairs of public and private keys, each of which have their own balance and transaction history and reflect the transaction history of the wallet’s owner. Figure 1 below shows some of the ways in which crypto currencies can be used.
Figure 1: What Is Cryptocurrency Used For?
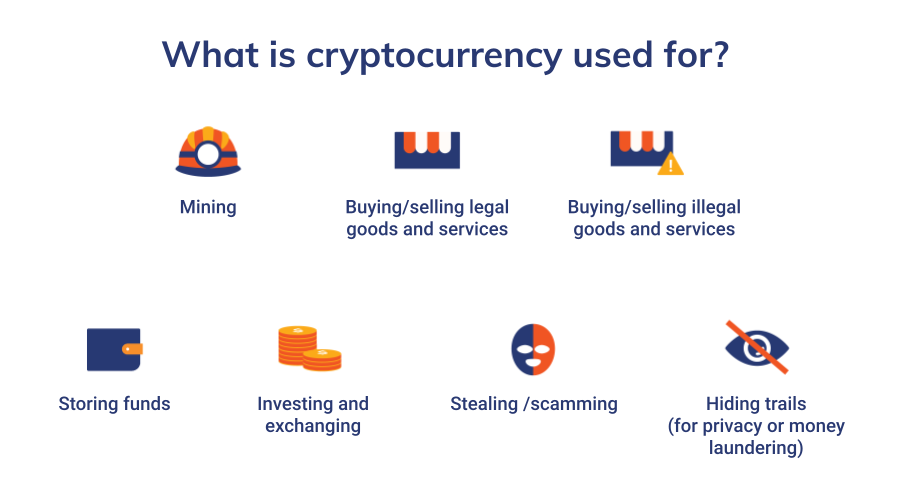
Each of these use cases and their associated services and organizations have their own risk of exposure to illicit activity. It is important to note that these risk levels only represent the services themselves and are not enough on their own to assess the risk level of a specific entity. The only way to do that is to analyze each cryptocurrency transaction and counterparties for each entity or service in greater detail (see Figure 2 below).
Figure 2: Potential for Criminality
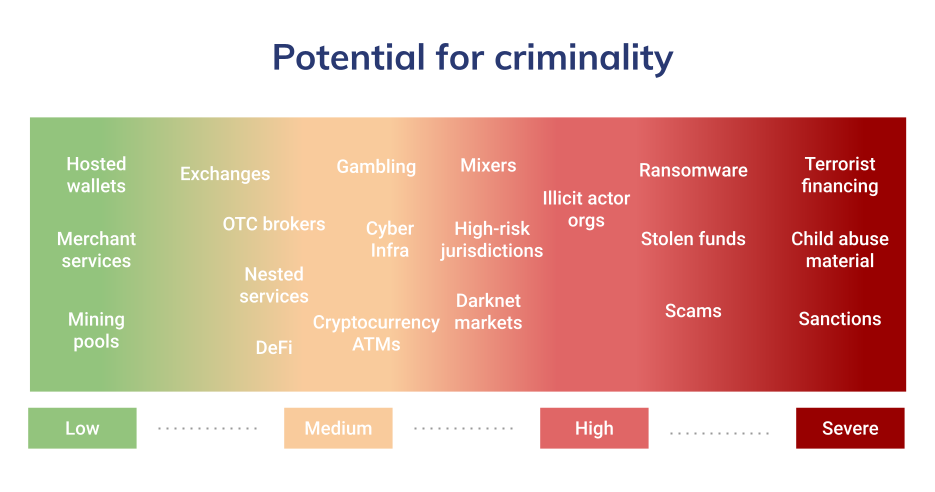
Services such as hosted wallets and merchant services, which are used less often for illicit activity, pose a lower risk, whereas terrorist financing schemes are illegal under any circumstances and severely risky. Those in the middle are not universally considered illegal but are often linked to or used to aid in criminal activities. For example, while gambling is perfectly legal in many jurisdictions, it has also historically been used as a means of money laundering.
But that is not all that compliance professionals need to know about cryptocurrency.
Cryptocurrency Is Not Anonymous
Cryptocurrency skeptics and public officials have expressed concerns about cryptocurrency’s anonymity, but this is a misconception. Cryptocurrency is in fact pseudonymous rather than anonymous. As explained above, users’ cryptocurrency balances and transaction histories are associated with unique addresses—also known as public keys—and are easily viewable on public blockchains(see Figure 3 below).
Figure 3: Visualizing a Cryptocurrency Transaction
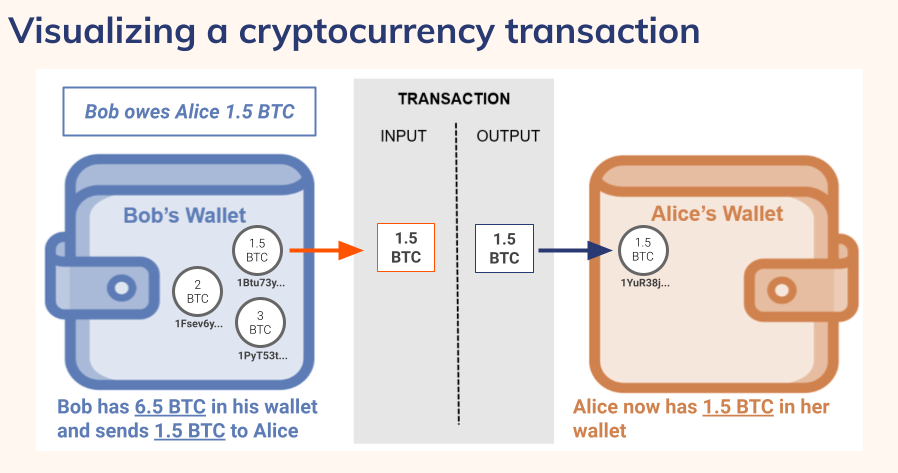
In this way, cryptocurrency transactions are actually more transparent than ordinary financial transactions. Once recorded on the blockchain, records of transactions stay there permanently and can be viewed at any time, even years later. However, what is not immediately visible on the blockchain is the real-world name of the individual or entity conducting a transaction. Does that make cryptocurrency anonymous? No, but it does mean there are further steps to be taken to determine who is behind a suspicious cryptocurrency transaction.
Furthermore, in most jurisdictions, cryptocurrency services are regulated similarly to financial institutions(FIs),2 meaning know your customer (KYC) information must be collected and checked and suspicious activity must be reported. This allows for the identification of the individual service where a user is conducting a suspicious transaction.
Cryptocurrency Impacts All Major Forms of Criminal Activity
Based on available data, blockchain analysis shows that just 0.34% of cryptocurrency transaction volume in 2020 was identified as associated with criminal activity.3 Despite that low share, cryptocurrency’s pseudonymous nature and capacity to carry out transactions outside the traditional financial system is appealing to many types of criminals. As a result, cryptocurrency is increasingly playing a role in nearly every type of criminal activity that matters to AML professionals. This should not be surprising. Criminals have always been early adopters of technology and cryptocurrency is no exception. Table 1 below describes some forms of criminal activity involving cryptocurrency.
Table 1: Criminal Activity Involving Cryptocurrency
| Type of Crime | How Cryptocurrency is Involved | Examples |
|---|---|---|
| Trafficking | Darknet markets are online, cryptocurrency-based marketplaces where users buy and sell drugs, stolen data and tools used for hacking. | Prominent darknet markets include Hydra,4 Empire Market and UNiCC. |
| Fraud | Scams are by far the most prominent form of cryptocurrency-related crime, with fraudsters taking in over $2.6 billion worth of cryptocurrency in 2020.5 Most cryptocurrency scams function similarly to conventional investment scams or Ponzi schemes seen in the fiat world. | Recent prominent cryptocurrency scams include Mirror Trading International, Jenco and the infamous Plus Token Ponzi scheme.6 |
| Child sexual abuse material (CSAM) | More than $2 million in cryptocurrency payments has been tracked to addresses associated with known CSAM distributors between 2015 and April 2020.7 | Darknet website Welcome To Video was the largest cryptocurrency-based CSAM marketplace ever observed until authorities took it down in 2019, arresting both its owner and more than 300 of its users across 38 countries.8 |
| Terrorism financing and sanctions | Designated terrorist groups have begun using cryptocurrency to solicit donations. In addition, some individuals and entities on the Office of Foreign Assets Control Specially Designated Nationals list see cryptocurrency as a means of circumventing sanctions. | Last year, U.S. authorities disrupted cryptocurrency-based donation campaigns carried out by al-Qaida and Hamas.9 Heavily sanctioned governments such as those in Venezuela10 and Iran11 have encouraged cryptocurrency infrastructure development as a means of bypassing U.S. sanctions. |
| Corporate and organizational extortion | Ransomware is a relatively new type of cybercrime in which bad actors deploy malware to encrypt the computer files of a victim organization, rendering them virtually unable to operate, until the organization pays a ransom in cryptocurrency. | Ransomware activity spiked dramatically in 2020, with attackers extorting over $400 million worth of cryptocurrency. Notable strains include Ryuk, Sodinokibi and DarkSide. |
Cryptocurrency Is Here to Stay
Skeptics have been predicting cryptocurrency’s demise for more than a decade and have continuously been proven wrong. Uncertainty and volatility are common to the emergence of any new asset class and that has certainly been true for cryptocurrency. However, public officials and leaders in the financial world have acknowledged the significance and the potential role that cryptocurrency will play in the world’s financial future.
What remains to be seen is how government regulation of cryptocurrency will evolve as the asset class continues to grow. So far, Financial Action Task Force (FATF) member states have regulated cryptocurrency businesses similarly to traditional FIs and money services businesses, requiring them to conduct KYC checks and follow suspicious activity reporting protocols. In the U.S., the Financial Crimes Enforcement Network (FinCEN) and other regulatory bodies have since weighed enacting stricter requirements around transactions involving unhosted wallets not associated with exchanges or other centralized cryptocurrency services.12 In addition, many governments are now considering central bank digital currencies (CBDCs), which would act as digital, tokenized versions of countries’ national currencies complete with their own purpose-built blockchains.
As cryptocurrency adoption continues to grow, so will scams, fraud and other cyber and ransomware extortions involving cryptocurrency. Criminals will also deploy a greater level of sophistication by utilizing the blockchain to move funds instantaneously across borders to evade detection, taxation and launder the proceeds of their crimes.
AML professionals must stay on top of the rapidly developing regulatory and cryptocurrency landscape to ensure that their organizations remain compliant in their dealings with cryptocurrency and are able to identify and mitigate risks. Furthermore, the public and private sectors will need to continue working together to establish regulatory frameworks and investigative techniques to keep the cryptocurrency and global financial ecosystem safe.13
- “Crypto Crime Summarized: Scams and Darknet Markets Dominated 2020 by Revenue, But Ransomware Is the Bigger Story,” Chainalysis Blog, January 19, 2021, https://blog.chainalysis.com/reports/2021-crypto-crime-report-intro-ransomware-scams-darknet-markets
- “Information on Complying with the Customer Due Diligence (CDD) Final Rule,” Financial Crimes Enforcement Network, https://www.fincen.gov/resources/statutes-and-regulations/cdd-final-rule
- “Crypto Crime Summarized: Scams and Darknet Markets Dominated 2020 by Revenue, But Ransomware Is the Bigger Story,” Chainalysis, January 19, 2021, https://blog.chainalysis.com/reports/2021-crypto-crime-report-intro-ransomware-scams-darknet-markets
- “Investigating Hydra: Where Cryptocurrency Roads All Lead to Russia and Go Dark,” Flashpoint, May 25, 2021, https://www.flashpoint-intel.com/blog/chainalysis-hydra-cryptocurrency-research/
- “Crypto Crime Summarized: Scams and Darknet Markets Dominated 2020 by Revenue, But Ransomware Is the Bigger Story,” Chainalysis, January 19, 2021, https://blog.chainalysis.com/reports/2021-crypto-crime-report-intro-ransomware-scams-darknet-markets
- “PlusToken Scammers Didn’t Just Steal $2+ Billion Worth of Cryptocurrency. They May Also Be Driving Down the Price of Bitcoin. [UPDATED 3/12/2020],” Chainalysis Blog, December 16, 2019, https://blog.chainalysis.com/reports/plustoken-scam-bitcoin-price
- “Making Cryptocurrency Part of the Solution to Human Trafficking,” Chainalysis Blog, April 21, 2020, https://blog.chainalysis.com/reports/cryptocurrency-human-trafficking-2020
- “Chainalysis in Action: DOJ Announces Shutdown of Largest Child Pornography Website,” Chainalysis Blog, October 16, 2019, https://blog.chainalysis.com/reports/chainalysis-doj-welcome-to-video-shutdown
- “Chainalysis in Action: Department of Justice Announces Takedown of Two Terrorism Financing Campaigns with Help from Blockchain Analysis,” Chainalysis Blog, August 13, 2020, https://blog.chainalysis.com/reports/cryptocurrency-terrorism-financing-al-qaeda-al-qassam-brigades-bitcointransfer
- “Hyperinflation and Sanctions Evasion: What On-Chain Data Tells Us About Venezuelans' Trust in Cryptocurrency” Chainalysis Blog, August 27, 2020, https://blog.chainalysis.com/reports/venezuela-cryptocurrency-market-2020
- “Iran uses crypto mining to lessen impact of sanctions, study finds,” Reuters, May 21, 2021, https://www.reuters.com/technology/iran-uses-crypto-mining-lessen-impact-sanctions-study-finds-2021-05-21/
- Nikhilesh De, “FinCEN’s Proposed Crypto Wallet Rule Might Hit DeFi,” CoinDesk, December 23, 2020, https://www.coindesk.com/fincen-wallet-rule-defi
- Want to learn more about who’s using cryptocurrency? Download Chainalysis’ latest report to learn everything AML pros need to know about the key service types and organizations that make up the cryptocurrency ecosystem.