Fraud and money laundering go hand in hand and fraudsters are early adopters of new money laundering opportunities; as participation in the cryptocurrency space gains momentum, so does fraud. This is not surprising as cryptocurrencies (virtual assets) can be lucrative, easily interchangeable and moved while being fairly unregulated in some parts of the world. They also offer increased anonymity, thus making them an attractive vehicle to illicit actors. Arguably, the most publicized and notorious form of fraud taking place in the cryptocurrency space is the hacking of cryptocurrency providers—essentially a coordinated theft of a large sum of funds.
The above noted fraud is one coordinated on a macroscale; however, less notorious and less known to professionals and cryptocurrency investors alike is small-scale microfraud. Such fraud primarily occurs due to fraudsters consistently developing new techniques that take advantage of both security flaws and users’ lack of technical knowledge. This article discusses some of the recent fraud typologies in the cryptocurrency industry, which have resulted in thousands of users losing their cryptocurrency investments, and the steps that can be taken to avoid falling victim to these techniques.
Cold Storage and Counterfeit Products
Cold storage wallets are physical cryptocurrency wallets that, as opposed to “hot” wallets, are not connected to the internet. The most popular cold wallet used is often a USB-type stick. As seen with the recent cases of DragonEx, Binance and Bithumb, cryptocurrency exchanges—even the most well-known and highly trusted players in the industry—can fall victim to hacks and subsequent cryptocurrency theft. This leaves users with now empty accounts, and little chance of recuperating their stolen funds.
To mitigate against macrofraud manifested in exchange hacks, cryptocurrency investors should move their funds to cold storage mediums after concluding their trading and investing activities conducted on various cryptocurrency platforms. As a best practice, cryptocurrency vendors should highlight this—in layman’s terms—in their terms of services and reinforce the message through their front lines. This will not only improve their customers’ experience but also decrease the impact of a hack.
For individual cryptocurrency investors, it is financially savvy to move funds to custody in the form of a cold storage wallet. Having said that, cold wallet storage users have to be aware that there are still fraud risks associated with the most popular cold storage form, the USB stick. For example, if buying a crypto wallet from a third party (i.e., not the manufacturer to save a few bucks), there is the risk of buying a counterfeit product. In the fiat world, counterfeit products might not perform as intended or look different to the original ones; in the crypto world, one may lose thousands in financial holdings. With counterfeit crypto wallets, whilst there are telltale signs, fraudsters have come close to perfection with packaging and the red flags might not be apparent to the untrained eye.
One of the red flags associated with USB cold storage is receiving pre-set written recovery instructions with an ordered wallet USB package. Fraudsters can access wallets by leading the user to punch in a pre-set phrase included on a “scratch off” to receive a 24-word recovery seed phrase. For new cryptocurrency adopters, a seed phrase, seed recovery phrase or backup seed phrase is essentially a list of words that store all the information needed to recover a wallet. In the case of an authentic product, this recovery method is usually automated and not manual. If a device comes with any form of pre-set instructions and the new user enables them, another individual might have received access to the new user’s device. Once the new user plugs in to transfer funds to the device, funds can be depleted since another individual can access the wallet. Therefore, new users should order from the original manufacturer to guarantee that whatever is used to store funds is authentic and uncompromised from the start.
Cybercrime and Cryptocurrency
Every internet user has heard the same advice—consistently update passwords, do not open suspicious links or emails, keep software and operating systems up-to-date, and monitor credit scores to make sure it is reflective of financial standing. Following these guidelines can greatly reduce the risk of becoming a victim of security breaches and suffering financial, reputational or data loss. For cryptocurrency users, a security breach can be even more detrimental. The stolen data can be used to obtain a user’s virtual assets, making the above advice more a set of strict rules to follow.
Unfortunately, even the most security-conscious cryptocurrency user may fall victim to malicious browser extensions. Browser extensions are convenient pieces of software downloaded from the internet’s favorite browsers (Chrome, Firefox, etc.) and used by millions to improve their internet browsing experience, such as downloading ad blockers to remove advertisements when visiting websites. Although convenient, these extensions act as potentially malicious doorways to computers and allow the administrators of the extensions access to very sensitive information that can be leveraged by bad actors.
Some of this sensitive information can include users’ usernames and passwords to email accounts utilized to access as well as verify accounts on cryptocurrency exchanges, where the virtual assets of users are often stored. Having obtained these credentials, bad actors can log into the compromised users’ accounts and withdraw the funds to their own cryptocurrency addresses and these transactions cannot be reversed.
Many victims wonder how their account credentials were stolen often without considering that the browser extensions they downloaded may be operated by illicit actors or that the extension itself may have been compromised, giving the hackers unauthorized access to user information. A perfect example is the MEGA Google Chrome extension. In September 2018, the extension was compromised as it was being used to siphon off user login credentials and cryptocurrency private keys.
Users should regularly scan for unwanted browser extensions
The remedy for cryptocurrency users is to conduct thorough due diligence before downloading any browser extension. If possible, limiting the number of extensions may further decrease the risk of being exposed to potential hacks. As seen by the MEGA extension hack, even reputable and well-known extensions are vulnerable to attacks. Users should regularly scan for unwanted browser extensions. There are abundant online tutorials showing step-by-step how to remove extensions safely. In addition—and this should apply to any account that contains login credentials—cryptocurrency users should enable a form of two-factor authentication (2FA) on email and cryptocurrency accounts. This can prevent illicit actors from logging in to user accounts, even if they have the correct username and password combination.
Microhacks aka Extraction Attacks
One of the downfalls of a security breach resulting in compromised credentials would be a bad actor obtaining access to cryptocurrency holdings stored with a cryptocurrency vendor, especially if holdings are not moved to cold storage.
Whilst hacking an exchange—essentially breaching multiple sophisticated safeguards deployed to protect against hacks—would require a sophisticated group of criminals, accessing individual accounts is a much more attainable target. Extraction attacks are essentially microhacks. Bad actors—usually less sophisticated as compared to macrohack attackers—will exploit a combination of compromised credentials and varied security settings of individual’s accounts to siphon funds from compromised accounts.
A bad actor who has access to a cryptocurrency investor’s credentials can simply access the user’s account on any of the cryptocurrency providers and withdraw funds, especially if no second layer of security (e.g., 2FA) is used to verify the account. A more cunning fraud would be to drain a cryptocurrency investor account with enabled security features that safeguard against unauthorized withdrawals but not against unauthorized trading.
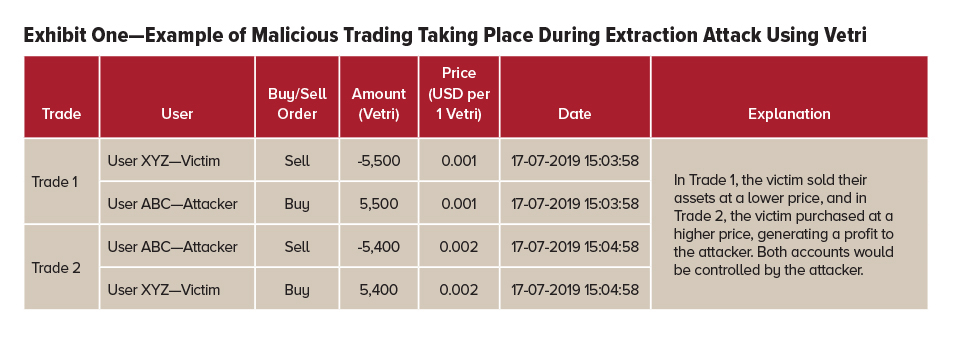
Perpetrators will usually open their own accounts with the cryptocurrency providers—more likely registering their accounts with encrypted emails and more commonly with disposable email addresses—and then trade against the victims’ accounts. For example, the perpetrator will force the sale position on the victim’s account and simultaneously place a buy order of an equivalent amount on the perpetrator’s account. In a subsequent trade, the perpetrator will sell the newly acquired cryptocurrency at a higher price to the compromised account and create a gain. This process repeats in a manner that “extracts” funds from the compromised accounts to the perpetrator’s account. The buy/sell trades are executed simultaneously and may be orchestrated using an automated trading program. The fraudsters will eventually withdraw the newly created positive balance generated through manipulative trading.
Extraction attacks typologies may vary as follows: one perpetrator on one victim, one perpetrator on many victims and many perpetrators on many victims. The typologies will vary given the number of compromised credentials available at hand; therefore, this kind of fraudulent activity is a crime of opportunity (i.e., whatever accounts fraudsters can compromise). Exhibit One above provides an example of malicious trading with the cryptocurrency Ventri. Another red flag of extraction attacks is trading in thinly traded coins. More often than not, triggering systems are risk-based and would monitor coins with high trading volumes as opposed to thinly traded coins. This way the fraudulent activity may go unnoticed for some time.
The remedy for cryptocurrency investors is to understand the security standards provided by their cryptocurrency vendor. Reputable vendors will offer layered security measures to authenticate the person conducting the activity. Sometimes cryptocurrency investors can avoid risk altogether by moving cryptocurrency to a personal wallet. By spending the extra fee to move the funds to a cold storage, investors will have secured funds technically under lock and key. It is also important to update login credentials and deploy all security features offered by cryptocurrency vendors for better protection against someone having unauthorized access to an account. For institutions, it is paramount to upgrade their detection systems to detect irregular activity for both thinly-traded coins as well as coins with high trading volumes and perhaps improve know your customer requirements, e.g., flagging accounts registered with disposable email domains or associated with anonymous browsers.
To conclude, whilst it is almost impossible to eliminate fraud risk affiliated with dealing with cryptocurrency fully, both individuals and the cryptocurrency industry players can outsmart fraudsters. For the industry players, this can be done by adopting and creating industry-wide best practices, tailoring security measures to safeguard different product features and continuously investing in technology that monitors outlier activity. For individuals, it is of absolute importance to stay tuned to the latest updates from cryptocurrency vendors and invest time as well as energy in safeguarding systems, as it is the only way to keep money safe.