
There is one constant in terrorism—the requirement for financing. There must be a steady stream of funds from the point of origin to the point of distribution. Whether the funding is required to sustain the operations of an organization or the activities of individual operatives, without money, terrorists are challenged and less likely to succeed. Between the sources and disposition of funds are the methods of moving money from the point of origin to the point of distribution. In a perfect world, it would be simple to trace funds from their origin to their disposition. Unfortunately, the myriad of financial sources, methods of movement and access points make identifying and tracing terrorist financing extremely difficult and time-consuming. There are seemingly infinite funding variations. This problem is further exacerbated by whether the funds are flowing to organizations or individual operatives. Funding streams to organizations or individual operatives tend to be vastly different due to the financial requirement levels specific to each.
Professional sports are played at a fast and constant pace. Inexperienced players frequently have trouble keeping up with the speed of the game. As they mature in their sport and gain experience, the game slows down in their minds, and they are able to successfully adjust to the pace of play. A great example of this maturation process is the rookie quarterback in the National Football League (NFL). Coaches and sportscasters frequently speak about the game slowing down and the young quarterback picking up the pace and the flow of the opposing defensive team. Analogous to the speed of professional sports is the pace and process of the funding flows to terrorists. To slow the flow of money down, it must be visualized from the source of funds through the methods of moving funds to the access points where money is distributed. This requires a sense of situational awareness from a terrorist-financing perspective.
In addition to foreign terrorist organizations, domestic violent extremist movements collectively pose a steady threat of violence
and economic harm to the U.S.
Situational awareness usually applies to being aware of one’s physical surroundings from a personal safety and security perspective. The concept of situational awareness can be applied to other areas of concern, such as financial crimes and terrorist financing. Situational awareness from a terrorist financing perspective should focus on the threat, who is being dealt with, organizations or individuals, and the funding flows required to support organizations or individuals, which will tend to be vastly different. The threat environment deals with the nature of the threat, as well as current and emerging trends. Anti-money laundering (AML) professionals will be dealing with either organizations or individuals. Funding flows deal with the sources, methods of movement and access to funds, as well as the funding streams to organizations, operations and individuals. Much like a young NFL quarterback gaining experience and slowing the game down in his mind, when the threat environment is understood and AML professionals recognize who they are dealing with, the pace or process of money movement can be understood and slowed down and the flow of funds from the point of origin to the point of distribution can be better visualized.
The Threat
On May 16, 2018, at a budget hearing, FBI Director Christopher Wray testified before the U.S. Senate Appropriations Committee, Subcommittee on Commerce, Justice, Science, and Related Agencies. In his testimony, with respect to counterterrorism, Director Wray stated: “From a threat perspective, we are concerned with three areas in particular: those who are inspired by terrorist propaganda and feel empowered to act out in support; those who are enabled to act after gaining inspiration from extremist propaganda and communicating with members of foreign terrorist organizations who provide guidance on operational planning or targets; and those who are directed by members of foreign terrorist organizations to commit specific, directed acts in support of the group’s ideology or cause.”1
Further, Director Wray testified that the FBI views the Islamic State in Iraq and Syria (ISIS) and homegrown violent extremists as the main terrorist threats in the U.S. He also pointed out the threat posed by ISIS foreign fighters, including those recruited in the U.S. Director Wray highlighted how proficient ISIS is at exploiting social media for recruiting and radicalizing vulnerable persons of all ages to either travel or to conduct a homeland attack. Director Wray stated that in addition to ISIS, al-Qaeda maintains its desire for large-scale attacks but currently does not have the capacity to do so. In the near term, al-Qaeda is more likely to focus on supporting small-scale, readily achievable attacks against U.S. and allied interests in the Afghanistan/Pakistan region. He also noted that, like ISIS, al-Qaeda seeks to inspire individuals to conduct attacks in the U.S. and the West. In addition to foreign terrorist organizations, domestic violent extremist movements collectively pose a steady threat of violence and economic harm to the U.S.
There is an evolution and devolution of the terrorism threat. Over the last year, ISIS has lost their caliphate in Iraq and Syria and has devolved from a military-like organization back to an insurgency. In the meantime, al-Qaeda is in the process of re-emerging as a more troubling global threat. Another threat to be cognizant of is the threat posed by Iran, a state sponsor of terrorism, and Hezbollah, their proxy. In addition to being a significant terrorist organization, Hezbollah is also one of the most proficient criminal organizations in the world. That is because they have built a strong hybrid terrorist and criminal infrastructure possessing a robust supply chain. The primary threat from Iran and Hezbollah is the threat they pose against Israel. There are many other Islamic terrorist groups who pose regional and country-specific threats throughout the Middle East, Africa, Asia and other parts of the world.
AML professionals must remain vigilant to the evolution and devolution of groups like ISIS and al-Qaeda and what that means to global, regional and more country-specific threats. There has been a major emphasis on the threat of Islamic terrorism over the last few years. As Director Wray mentioned in his testimony, AML professionals must remain cognizant and vigilant to the threat of domestic terrorism as well. Although Islamic terrorism is a more serious current threat, AML professionals must remain situationally aware of the threat of domestic terrorism. A constant reminder of the domestic terrorism threat is the bombing of the Alfred P. Murrah Federal Building in Oklahoma City, where 168 people were killed on April 19, 1995.
In the beginning of Director Wray’s testimony regarding counterterrorism, he differentiated three types of individual operatives: those inspired; those enabled; and those directed. From a terrorist-financing perspective, it is important to place what that means in the proper context. Those inspired will more likely be self-funded. Those enabled will be self- and/or terrorist-group-funded. Those directed will more likely be terrorist-group-funded and may also be self-funded.
Organizational or Individual Funding
Funding needed to support a terrorist organization and funding for individuals are distinctly different. Their funding streams and requirements will vary greatly. For terrorist financing, when visualizing the funding flow, distinguish between whether an organization or individuals are being dealt with. Money needed to sustain the operations of a terrorist organization will be far greater and more voluminous than what is required by individuals. This requires much greater bandwidth. When discussing terrorist financing, it is frequently heard that it does not cost much money to commit a terrorist attack. That is true. However, to run a terrorist organization requires considerable capital. This is why, when visualizing funding flows, distinguish between three funding streams: funding to an organization, funding to an operation, and funding to individual or group operatives.
From an organizational perspective, terrorist organizations should be likened to major corporations. In that context, look at the terrorist organization as a business and assess their business model. A business model is a plan detailing how an organization generates revenue and how it incurs cost. Terrorist organizations must continuously generate funds to cover expenses in order to sustain their operations. Much like a corporation, a terrorist organization must establish funding streams that adequately meet and ideally exceed the cost structure. Organizational revenue streams will include: revenue from business activity; locally raised revenue; and revenue from “traditional” terrorist financing, as addressed in Figure 1 in raising funds. The organizational cost structure will include: the cost of business operations; cost of governance; cost of terrorist operations, public relations and financial facilitation; and overhead costs.
Identifying an organization’s business model requires a mission statement. What does the organization aspire to be? This requires the desired infrastructure which will be contingent upon funding requirements and funding sources. Once funding requirements and funding sources align with revenue streams and cost structure, their mission statement can be focused to meet realistic aspirations. The last requirement of the business plan is to identify and exploit the funding mechanisms necessary to supply the required funds that meet or exceed operational expenses.
From the perspective of individual terrorist operatives, the role of the operative within or on behalf of the organization must be identified. The role or responsibilities an individual operative has will determine their financial requirements and the capacity in which they could interact with a financial institution. Individual operatives will include leaders, fundraisers, facilitators, recruiters, fighters, or homegrown violent extremists and others who play support roles. Each terrorist actor will have different and somewhat unique funding requirements from other actors. Thus, it is important to identify the role each terrorist actor is responsible for within or on behalf of the organization.
The more the money is moved and stored in the financial system, the more obscured and seemingly legitimate it becomes
Likewise, it is important to determine if individual operatives are inspired, enabled or directed by the organization. If they are members of the organization, they will most likely be directed by the organization. If they are acting on behalf of the organization, it is possible they are being directed, but more likely, they are enabled, or most likely, they are inspired by the organization. Those inspired by terrorist propaganda can be empowered to act in support or on behalf of an organization in a leaderless fashion. These individuals will most likely be self-funded. Those enabled to act are usually provided with guidance on operational planning or targets. These individuals will be self- or terrorist-group-funded. Those directed are more likely to be group members. These individuals will be terrorist-group-funded and in some instances, self-funded.
Funding Flows
The terrorist funding cycle is to raise, move, store and spend money. Money laundering is a three-step process consisting of placement, layering and integration. To better visualize the flow of funds from point of origin to point of distribution, the visualization process must be slowed down much like an inexperienced quarterback learns to slow down the flow of the opposing team’s defense. Simplify the process as much as possible. This can be quite challenging in view of the many variations one may be confronted with. A good gauge is to assess the funding flow in two steps. The first step is to visualize and compare the terrorist funding cycle with the money laundering process. The second step is to visualize and assess the funding flow through each of the four elements of the terrorist funding cycle in a progressive and detailed manner.
Placing the terrorist funding cycle in conjunction with the process of money laundering is the first step in visualizing funding flows. Raising and moving money represents placement, where funding is placed into the financial system. Moving and storing money, and possibly continuing to move and store money, represents layering. The more the money is moved and stored in the financial system, the more obscured and seemingly legitimate it becomes. From storing to spending, the money represents integration. This is where the funds are accessed and distributed to support terrorist activities.
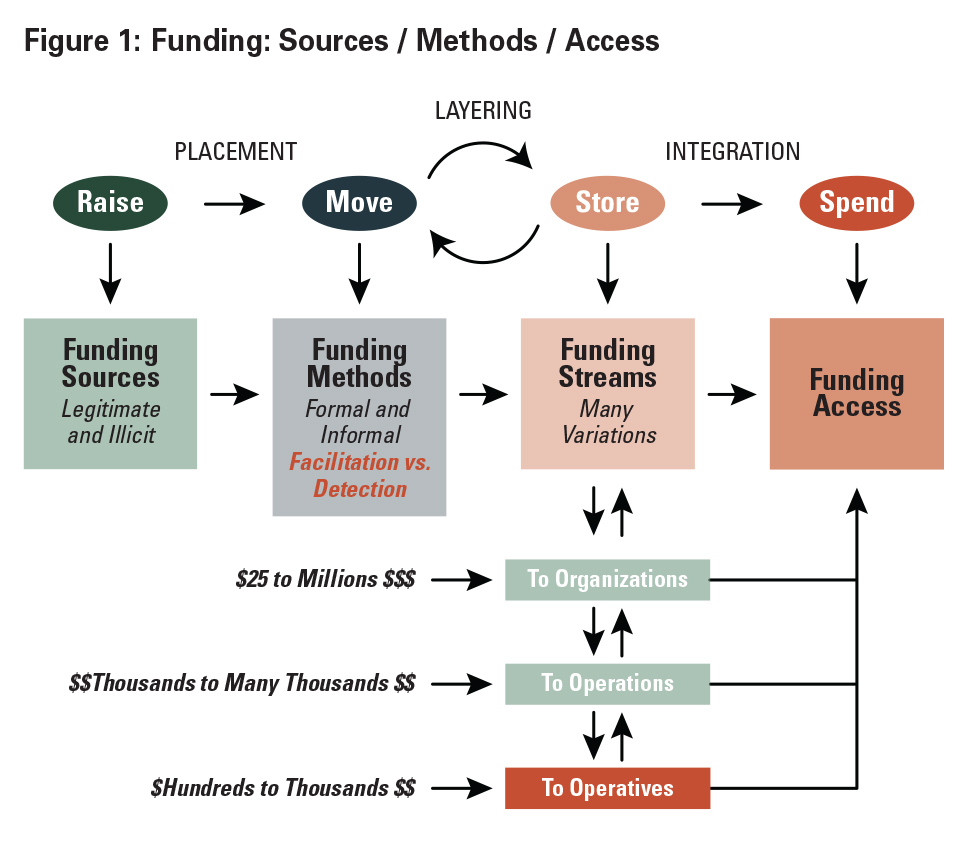
The second step is to visualize each element of the terrorist-funding cycle (raise, move, store and spend) step-by-step from the source of funds to the distribution of funds, as follows:
- Raise ➞ The source of funds will either be legitimate or illicit. Legitimate funding sources include private donations and legitimate commercial enterprises. Illicit funding sources include the full gamut of criminal activities ranging from theft, trade, drug trafficking, kidnapping, taxation or extortion, and state sponsors, most notably Iran.
- Move ➞ Funding methods include use of both the informal and formal financial systems. Terrorists will use both systems to ensure there is a consistent flow of funds to sustain their ability to function. This will include bulk cash; hawala and/or illegal money remitters; barter and/or trade; money exchangers; financial institutions, including banks, correspondent banks and money services businesses; use of wire transfers and automated clearing house payments; use of credit, debit and stored value cards; use of the internet, mobile devices and virtual currencies; and use of other vehicles to include shell and front companies, charities and other mechanisms. All of these mechanisms serve as facilitation tools. A critically important consideration is that financial institutions serve as facilitation tools or detection mechanisms. This is where AML compliance professionals find themselves on the front line in the fight to disrupt terrorist financing. AML professionals must do all they can to advance and enhance detection and diminish facilitation through financial institutions.
- Store ➞ There are three primary funding streams that support terrorism. The problem and challenge is there can be many variations to the three primary funding streams. The key for terrorists is having direct access to funds at select intervals between points of origin and points of distribution. Coupling the differing types of terrorist actors with the multiple variations of the three primary funding streams can become a daunting challenge. This is where it is extremely important to differentiate between funding supporting organizations and funding supporting individuals. It is important to try to simplify the funding flow as much as possible back to the point of origin and forward to the point of distribution. The first funding stream is funding that flows to a terrorist organization. Money that flows to an organization can range from as little as $25 to millions of dollars. This requires considerable bandwidth. It takes considerable financing to sustain a terrorist organization. The second funding stream is from an organization to support an operation. Funding that flows from an organization to an operation will range from a few thousand dollars to many thousands of dollars. Funding is either sent directly from the organization to operatives, or more likely through facilitators to the operators. The third funding stream is funding from the organization, through the operation to individual operatives, cells or affiliate groups. Funding that flows to operatives, cells or affiliated groups typically ranges from hundreds to low thousands of dollars. With the growth of homegrown violent extremists, especially those inspired by terrorist organizations, there has been an emerging variation in the form of a reverse flow. In these instances, the inspired individuals or cells are self-funded by various means to include entitlement funds or otherwise legitimate salary income.
- Spend ➞ Understanding if one is dealing with an organization or individuals will help focus on which funding stream is involved. In the sports analogy, this slows down the pace or process of the money movement and better visualizes the flow of funds from points of origin to points of distribution. Determining which of the three primary funding streams is used to access funds will more likely identify the point of distribution and amount disseminated. Funds flowing to the organization will usually range from minimal amounts to millions of dollars. Funds flowing to operations will probably be in the low thousands to the many thousands of dollars. Funds flowing to operatives will typically range from hundreds to low thousands of dollars. Understanding and visualizing the process of flow of each of the three primary funding streams will slow the process down and enhance the prospect of detection.
To succeed in disrupting terrorist financing, visualize the flow of funds from the point of origin to the point of distribution
Conclusion
Financing poses a stark contrast for terrorists. On one hand, finance is the lifeblood of a terrorist organization. On the other hand, finance is one of the biggest vulnerabilities confronting terrorists. The more that can be done to disrupt the flow of funds, the more that can be done to prevent terrorism. Disrupting their funding flow impedes or prevents the ability of terrorist organizations and/or individual terrorist operatives to conduct terrorist activities. There are three primary terrorist funding streams: funding to an organization; funding from an organization to support an operation; funding from the operation to operatives. The challenge AML professionals face is that there are an infinite number of variations in the three primary funding streams.
To succeed in disrupting terrorist financing, visualize the flow of funds from the point of origin to the point of distribution. The pace and the volume of the funding flow can be overwhelming. What is needed is to simplify and slow the pace and process of visualization down. Much like the sports analogy of an inexperienced athlete, especially an NFL quarterback slowing the speed of the game down to read the opposing defense, AML professionals should slow the pace of the funding flow down by visualizing the funding stream and being situationally aware of the threat environment and who they are dealing with, organizations or individuals.
The funding flow should be assessed in two steps:
- Visualize and compare the terrorist funding cycle (raise, move, store and spend) with the money laundering process (placement, layering and integration).
- Visualize and assess the funding flow in a progressive manner through each of the four elements of the funding cycle, as follows:
- Raise ➞ Assess funding sources
- Move ➞ Assess funding methods
- Store ➞ Assess funding streams
- Spend ➞ Assess funding access
When it comes to terrorist financing, like criminal money laundering, financial institutions serve as either a facilitation tool or a detection mechanism. AML professionals must do all they can to minimize facilitation and maximize detection, especially in the quest to disrupt terrorist financing. Understanding the threat environment, recognizing who is being dealt with and visualizing the flow of funds will enhance detection. This will enable AML professionals to exploit the financial vulnerability of terrorists instead of them exploiting the financial system.
For more information on how to identify and mitigate terrorist financing, please visit: http://www.acams.org/counter-terrorist-financing-training/.
- “State of Christopher A. Wray Director Federal Bureau of Investigation Before the Committee on the Judiciary U.S. House of Representatives at a Hearing Entitled ‘Oversight of the Federal Bureau of Investigation’,” House Judiciary Committee, December 7, 2017, https://judiciary.house.gov/wp-content/uploads/2017/12/Director-Wray-Testimony.pdf











Very Informative and Interesting